Ten case studies, ten cyber attacks of machine learning
Artificial intelligence (AI) and machine learning (ML) are the subject of many debates, especially in the cybersecurity community. So, is machine learning the next big security trend? Is artificial intelligence ready to accept machine learning-driven attacks? In general, is artificial intelligence ready for use? No matter what you think about whether machine learning will become a cybersecurity savior, there are two things that are true: one is that analysis has a place in the security field, and the other is that machine learning represents what we can do today in some specific use cases. The best answer given.
Although there are reports that hackers use the "complexity" approach to intrusion, it is very likely that hackers or hacker groups have cleverly used common attack methods to break into the screen giant's system and used "little.finger66". "(Annotation: "Little Finger 66", "Little Finger" is the nickname of "The Game of Power" episode of the character Petit. Berri's nickname.

Here are some use cases that represent some of the common security threats that affect every business. However, machine learning may or may not be a panacea for cybersecurity, but it will certainly help in the following situations.
Use case 1: "Forkfish" (prevent phishing)
Phishing is the most common attack vector today and it is very successful. This type of attack takes advantage of personal familiarity with communication tools, such as social media and email, to send malicious content to unsuspecting recipients via attachments or links. The effectiveness of such an attack relies on the ability of the attacker to mislead the end user to click or download the malicious payload and then bypass the internal controls. This increasing attack and ransomware payloads make this attack even more serious.
Organizations can detect these threats by capturing metadata from emails, and this does not affect user privacy. By looking at the email header and subsampling the message body data, the machine learning algorithm can learn to identify email patterns that can expose malicious senders. By extracting and marking these microscopic behaviors, we can train our model to detect if someone is trying phishing. Over time, machine learning tools can build graphs based on the sender's trustworthiness.
Use Case 2: Watering Holes
Similar to phishing attacks, puddle attacks seem to be legitimate websites or web applications. However, these websites or applications, while real, may have been stolen, or are simply fake websites or applications designed to lure unsuspecting visitors into personal information. This type of attack also depends in part on the ability of the attacker to mislead the user and effectively attack the service.
Machine learning can help organizations benchmark web application services by analyzing data such as path/directory traversal statistics. Algorithms that learn over time can identify common interactions between attackers or malicious websites and applications. Machine learning can also monitor the behavior of rare or unusual redirection patterns, which can point to site hosts or from site hosts, and can also monitor referral links – all of which are typical risk warning indicators.
Use Case 3: Intranet Roaming (Lateral Movement)
This is not a specific type of attack. The intranet roaming attack method indicates the attacker's movement in the network. This is because they are looking for vulnerabilities and applying different technologies to exploit these vulnerabilities. Intranet roaming can particularly indicate that risk rises along the kill chain – the attacker's activity from reconnaissance to data extraction – especially when the attacker moves from a lower-level user's machine to a more important person who has access to valuable data.
A web traffic entry record tells you how your visitors interact with your site. Machine learning understands the context of data and can dynamically provide a view of normal communication data. With a better understanding of typical communication flows, the algorithm can perform change point detection (that is, when the probability distribution of a given communication mode changes and becomes less likely to be a "normal" communication activity, It can be identified) to monitor potential threats.
Use Case 4: Covert Channel Detection (Covert Channel DetecTIon)
An attacker using a covert channel transmits information over a channel that is not used for communication. The use of covert channels allows attackers to maintain control over threatened assets and use tactics that can execute attacks over time and are not discovered.
Attacks that use covert channels typically depend on the visibility of all domains on a given network. Machine learning techniques can capture and analyze statistical data about rare areas. With this information, the security operations team can more easily make cloud attackers look like they are. Without an overall understanding of the networks they intend to attack, it is more difficult for cybercriminals to push their attacks along the kill chain.
Use Case 5: Ransomware
The ransomware "is a real name." This malware erases the drive and locks the infected device and computer as a key point in exchange for the user's encryption key. This form of cyberattack locks the message until the user abandons his or, in some cases, threatens to post the user's personal information if the ransom is not paid.
Ransomware presents a challenging use case because attacks often result in a lack of evidence of network activity logs. Machine learning techniques can help security analysts track small behaviors associated with ransomware, such as entropy statistics or processes that interact with a given entire file system. Organizations can focus their machine learning algorithms on the initial infection payload in an attempt to identify these pieces of evidence.
Use Case 6: InjecTIon Attacks
The Open Web ApplicaTIon Security Project (OWASP) lists injection attacks as the number one security risk for web applications. (Note: The current version of OWASP Top-10 has been rejected and the organization has restarted data calls and investigations by security professionals). Injection attacks allow an attacker to make malicious input in a program. For example, an attacker would enter a line of code into the database and, when accessing the database, modify or change the data on the site.
Database logs are another source of information that can help identify potential attacks. Organizations can use machine learning algorithms to build statistical profiles of database user groups. Over time, the algorithm learns how these groups access individual applications in the enterprise and learns to discover the anomalies that occur in these access patterns.
Use Case 7: Reconnaissance
Before an attack is launched, the hacker conducts extensive investigations of the target or target group. Detection includes detecting vulnerabilities in the network. The attacker will investigate within the perimeter of the network or within the local area network (LAN). Typical detection attack detection uses signature matching techniques to find repetitive patterns that may represent malicious behavior through the network activity log. However, signature-based detection typically produces a bunch of noisy false alarms.
Machine learning can be a compass for network data topologies. Trained algorithms can develop such topologies to identify the propagation of new patterns, which is faster than signature-based methods. Using machine learning also reduces the number of false positives, allowing security analysts to spend time dealing with really important alarms.
Use Case 8: Web Trojan (Webshell)
The United States Computer Emergency Readiness Team (US-CERT) defines the Webshell as "a script that can be uploaded to a web server to remotely manage the machine." With remote management, an attacker can initiate processes such as database data dumps, file transfers, and malware installations.
The target of Webshell attackers is usually the back-end e-commerce platform through which attackers target the shopper's personal information. Machine learning algorithms can focus on statistics on normal shopping cart behavior and then help identify outliers or behaviors that should not occur at this frequency.
Use Case 9: Credential Theft (CredenTIal Theft)
Some high-profile attacks, including attacks on virtual private networks (VPNs), are the result of credential theft. Credential theft is usually done using means such as phishing or puddle attacks, where an attacker extracts login credentials from the victim to access sensitive information maintained by the organization.
Internet users – consumers – often leave a login mode. Websites and apps can track location and login time. Machine learning techniques can track these patterns and the data that contains them to understand what user behavior is normal and which behaviors represent potentially harmful activities.
Use Case 10: Remote Exploitation
Finally, many attack modes use remote exploits. These attacks typically operate through a series of malicious events against the target system to identify vulnerabilities and then provide payloads (such as malicious code) to exploit the vulnerabilities. Once the attack delivers the payload, it executes the code inside the system.
Machine learning analyzes system behavior and identifies instances of sequential behavior that are independent of typical network behavior. The algorithm can learn over time, alerting the security analyst about the transmission of the payload intended to exploit the vulnerability.
The discussion here is not the end of machine learning, but should be its starting point.
Accurate network security analysis systems must be the cornerstone of modern security operations centers. However, if there is no data sample, it is impossible to conduct an accurate analysis. Security teams that use machine learning thinking and use machine learning techniques can resolve these types of attacks faster. Machine learning or any other technology will never be the end and all of any industry. It does provide an alternative, open source philosophical thinking that can be used to identify and handle cyber attacks, which can improve many of the methods currently in use.
Open Frame For Resistive Touch All-in-one
Green Touch's self-developed 5A series of open frame touchscreen computers can support Windows, Linux, Android operating systems, with excellent functionality and flexibility, and provide you with reliable commercial and industrial-grade solutions. The 5A series adopts modules. Designed with diverse and powerful functions, it can be used in public environments such as in-store human-computer interaction, operating system cashiers, self-service, hotel services, and corporate offices. It has a wide range of uses, provides a variety of sizes and configuration options, and has versatility for cross-environmental use , sturdy and durable, can meet the needs of continuous public use.
* Display Type: Active Matrix TFT LCD, LED Backlight
* Touch Typeâ‘ :PCAP ,10 Points Touch
* Touch Typeâ‘¡:Infrared ,10 Points Touch
* Touch Typeâ‘¢:4 Wire Resistive/5 Wire Resistive,Single Touch
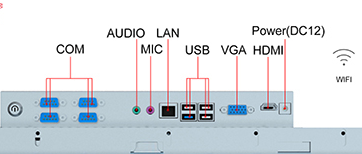
* Extra Video Output:1*VGA,1*HDMI
* Motherboard:Inter I3,I5,I7
* Supported OS:Windows,Android,Linux
* Certificates:UL,FCC,CE,CB,HDMI
* Warranty:1 Year


Open Frame Touch Computers,Open Frame Touch All In One PC,Open Frame Touch All In One Computer,Commercial All-in-one Machine
ShenZhen GreenTouch Technology Co.,Ltd , https://www.bbstouch.com