The Internet of Vehicles is in a state of flux, but it is the rhythm of losing your life.
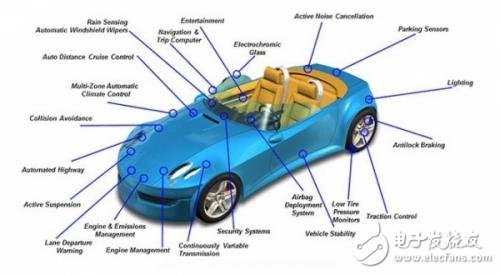
With the popularity of smart cars and car networking, there are more and more discussions about hacker threats to car safety, but most of the discussions and articles have no technical basis, and the discussion is often itch. The conclusion is naturally not reliable, so can the hacker To threaten our car safety, let's make an in-depth interpretation. In the current car, we almost never directly control the car through the mechanical device. After we step on the throttle, we do not directly control the throttle opening and closing through the wire, but the accelerator pedal sensor transmits the signal we stepped on to the driving. According to the induction, the computer controls the degree of throttle opening by the motor to achieve the purpose of accelerating the car.
The danger of a car being invaded
In the development and debugging of modern cars, many of them are software development work.
During the driving process, if the signal of the driving computer is disturbed, the driver is deprived of the control of the car, and the consequences are unimaginable.
In 2007, Toyota appeared in the United States with brakes. The US court heard testimony from embedded technology expert Michael Barr, an embedded systems engineer with more than 20 years of industry experience. In the 18 months, 12 embedded system experts, including Michael Barr, were entrusted by the plaintiff's litigation team and were locked in a highly secure room in Maryland for Toyota Power Control System software (mainly 2005). The Camry) source code for an in-depth review.
The final survey results are written in a detailed report on 800 pages and 13 chapters. In view of the confidentiality agreement, the content of the investigation has not been announced until the first partial disclosure of the Oklahoma trial.
The conclusion is actually very simple, because Toyota's electronic system design is flawed, stack overflow is easy to occur and there is not enough calibration correction. The simple problem in this computer field, when it appears in the car, may cause the throttle signal to lock up and the vehicle accelerates. All the throttle brakes failed, and the car continued to accelerate and could not stop, and eventually the car crashed.
Familiar with the field of information security, knowing that using data overflow is a common method for hacking systems. On the computer, on the phone. A hacker can gain control, gain access, and steal passwords. In the car, if the hacker gets the control area of ​​the driving computer, an order can make the whole car die.
In the face of a car whose accelerator has been accelerating, the brakes are out of order, and the direction is out of order, what can the people in the car do besides praying?
In January of this year, the German authoritative auto agency ADAC released a report on BMW's interconnected driving defects. The report said that hackers could use this vulnerability to wirelessly open the doors of BMW, Mini and Rolls-Royce cars within a few minutes. But even if this loophole is exploited, the car is hacked, and the owner is at most a car, without causing an accident.
Since car hackers can cause car crashes, why have we never heard of similar reports? This is because the current car network and autonomous driving are still in their infancy, and the car industry that is behind in information has protected car safety.
On the computer, in the era of backward technology, computers are not connected to the Internet. Even if there is a virus, it is limited to floppy disks and CDs. As long as the optical drive and floppy drive are shielded, the information of the computer can be secured. This is a physical isolation.
The current automobile industry is also the same. Most cars have driving computers, but driving computers are not connected to the Internet of Vehicles and the Internet. Although one of the data on the driving computer is wrong, it can be destroyed. But if you don't connect to the Internet, the hacker's ability can't modify your data. You can't blacken your car, but the car is safe.
However, the backwardness will eventually become advanced. With Tesla, Apple and Google Silicon Valley companies enter the automotive industry, the automotive industry will eventually enter the era of car networking and unmanned driving, while the Internet of Vehicles and the era of driverless means that car driving computers directly connected to the Internet, information Security is a problem, hackers can really be dead.
Backwardness is a kind of protection, but this protection is dying with the development of the times.
Featuring level VI energy efficiency and meet IEC/EN/UL 62368 safety standards for ITE/AV equipment, the external universal power adapter accepts the output voltage 15 Volt with universal AC input voltage range from 100-240VAC and provides 3 Years warranty. These series 15vdc power adapters use PC flame retardant material housing, all materials conform to the international environment protection standard. Protections for over voltage, over current and short circuit are also included.
15v dc regulated power supply,15v DC adaptor,110V 220V 230v 240V to 15v power adaptor,universal input 15v 3a adaptor
Shenzhenshi Zhenhuan Electronic Co Ltd , https://www.szzhpower.com