How does machine learning combat AI crime
Nowadays, the Internet is developing rapidly, and the issue of network security has become a big problem. Network security has brought a series of huge problems and different levels of challenges to different fields. Some expect that by the end of 2017, the global market value of cybersecurity will soar to 120 billion. This set of data has to cause people to ponder.
Data security has been and will continue to be an important area of ​​continuous improvement in different organizations. Like cat-and-mouse games, hackers are always looking for new ways to break into security systems; as such, security systems respond to a variety of attack strategies and tools through continuous self-upgrades.
Big DataWith the advent of artificial intelligence, many jobs are slowly being replaced by computers or robots. This does not refer to anti-virus software on the ordinary desktop, but imagine a scenario: if you have a large organization with thousands of employees. All computers within the organization generate PB-level logs that are stored in a database to record various daily activities and are then used for separate and associated threat analysis. These massive results have led to what we call "big data."
In 2012, Gartner defined big data as: “There is a need for new processing models to have greater decision making, insight, and process optimization capabilities with massive, high growth rates and diverse information assets.†Today, Gartner This 3V definition is still widely used, and everyone agrees that “these information assets with massive, high growth rates and diverse characteristics need to be transformed into value through specific technologies and analytical methods.â€
Machine learningWith the above definition of big data, the next step ahead of us is to analyze it. You can take different types of analysis to get your computer trained for specific purposes. This type of training is called "machine learning," which is the development of pattern recognition and artificial intelligence about computational learning theory.
Machine learning predicts data by exploring and researching the structure of the algorithm. Machine learning uses well-designed and pre-programmed algorithms to efficiently perform a complete set of computing tasks. Among the most common applications are: mail filtering, network intrusion detection, data leakage behavior involving internal malicious people, optical character recognition (OCR), learning to rank, and computer vision.
In many cases, the larger the size of an organization, the more difficult it is to have a cybersecurity task. That's why most large organizations have their own network security department. Let's take a look at some statistics about the size and type of threat.
malicious software
Malware is categorized as software that is specifically designed to interrupt, corrupt, or gain normal access to a computer system. In the third quarter of 2016 alone, a security company captured 18 million new malware samples, an average of 200,000 per day. Malware continues to evolve not only in speed but also in the level of bypassing anti-virus protection. These are beyond the reach of your company, IT team, and suppliers.
Ransomware
As the name suggests, such software locks the system's screen or user's files to block or restrict users from accessing the system until they pay a ransom. Since 2016, there have been 4,000 attacks by ransomware every day. This figure has increased by 300% compared to 1,000 per day in 2015.

Computer virus statistics
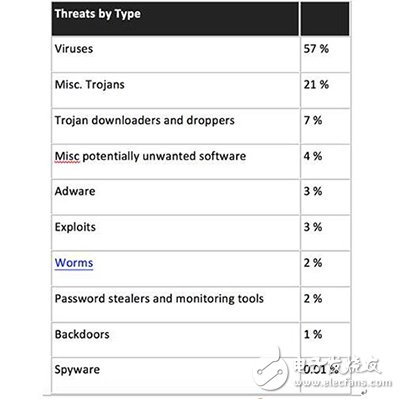
Threat type
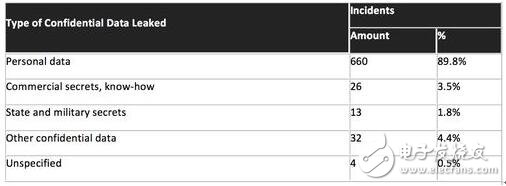
Leak type
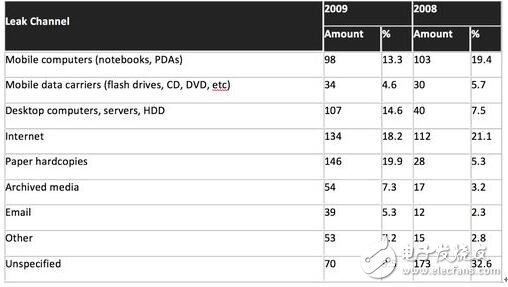
Now that we have realized that the cyber security departments of large organizations need to face billions of attacks every day from all kinds of malware, we must not only improve the security configuration, but also the ability to promptly alert when threats are encountered, and It is also necessary to be able to identify and classify threats so that users are fully aware of their situation.
Therefore, our security system cannot stop, but by correlating various types of event notifications to form a detective cues to guide users and show them the various situations in their dynamic systems. Clear image". We classify software for this purpose as SIEM (Security Information and Event Management), SEM (Security Event Management) or SIM (Security Information Management).
Of course, these terms are often used interchangeably to refer to such software in different scenarios. In order to achieve their high degree of customization and training, let's take a look at how machine learning is applied to combat cybercrime. Note that these smart software uses techniques such as deep learning, which we will discuss in the next section.
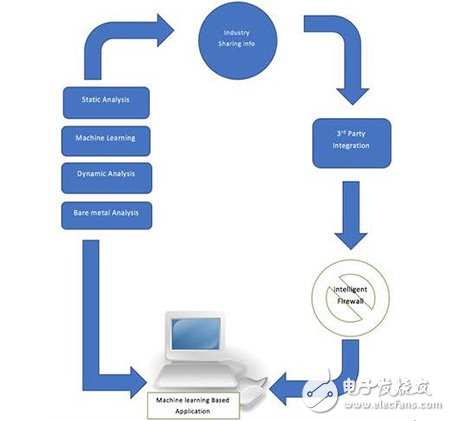
Threat Intelligence, Deep Learning and Artificial Neural Networks (ANN)
Generally speaking, individual malware is "easy to create and difficult to check." Once the system is able to identify it, it can “learn†how to respond to it next time. However, if you make minor modifications based on the original malware, the system is likely to be unrecognizable.
In fact, hundreds of new types of malware are rebuilt from a single piece of original software. So in this case, we need to use a different strategy to effectively create a secure area. There, the artificial neural network learns (gradually improves performance) by referring to various cases to complete tasks, and generally does not need to increase programming for specific tasks.
For example, at the time of image recognition, they learn to analyze and identify other images containing cats through multiple instances that have been manually labeled as "is a cat" or "not a cat." They also found that most applications are difficult to accurately represent using traditional computer algorithms based on rule programming.
In the field of network security, we can determine whether the various software is malware based on the level of similarity of the generic malware types that the system has been able to identify. Of course, in the case where the artificial neural network has not yet completed the "training", it is impossible to accomplish it overnight, and deep learning itself is a rather time consuming process.
Artificial neural networks (ANNs) are inspired by biological neural networks, which are implemented by a collection of connected units of so-called artificial neurons (similar to axons in biological brains). Each connection (synapse) between neurons can send a signal to another neuron. The (post-synaptic) neuron at the receiving end processes the signal and then sends its connection to its downstream neurons.
Neurons can usually use a real number between 0 and 1 to indicate their state. As the learning progresses, the weights of neurons and synapses also change, and this just reflects the intensity increase and decrease when it is sent to downstream signals. In addition, they can have a threshold and the downstream signal will only be sent when the aggregated signal is below (or above) the value.
Normally, neurons have a multi-layered structure. Different levels can perform different types of conversions based on their different inputs. The signal starts at the first (input) layer and may go through the multiple (multiple) traversal to the last (output) layer.
A single-layer feedforward artificial neural network, as shown in the following figure:
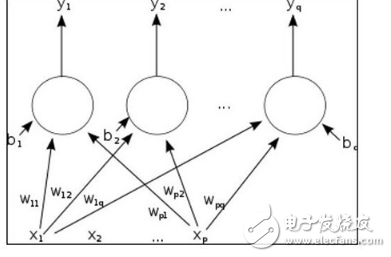
Single layer feedforward
The double-layer feedforward artificial neural network is shown in the following figure:
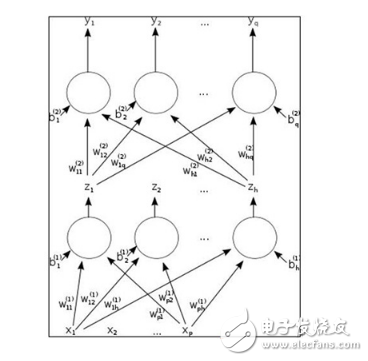 Double feedforward
Double feedforward
Therefore, we must provide all available information about malware to SIEM software, so that it can identify the existence of all different types of malware, and achieve a certain degree of malicious according to the established smart standards. The software is classified. This will increase the entire learning process to an advanced level that requires only half manual supervision or even manual supervision.
Through the above analysis, we have learned how SIEM is detected and protected from the outside. But in the security arena, we have another aspect to consider, that is, internal threats.
Now let's consider an example: Suppose any employee becomes a victim of a phishing attack when using a VPN to complete a task. His username and password information is stolen and the system is facing a data breach. So for SIM, as long as it sees these unusual personal behaviors, or a series of activities, it should be able to link them to point to and match those abnormal or dangerous data leaks and cross-border transfers. Case.
The SIM must have a system that is sufficiently advanced to understand and analyze the various behaviors of the user and the environment, by associating different activities to create a so-called "attack chain." The attack chain here refers to the identification of the overall event "chain", which includes: who, what, where, when, why, how to detail the current event, and finally give the current state of the event clear view.
These can help the user to know information such as what happened and what has been confirmed. The information provided by the system is valuable. They can help users further feedback to artificial intelligence such as timelines and impact levels, and ultimately allow the system to categorize millions of common events, mark thousands of "abnormal events", and then determine Several of them are true “attacksâ€, which in turn provide all “attack chains†that are confirmed by the ANN and contain diagrams.
in conclusionThe various advantages of artificial intelligence technology can be applied to the current network security infrastructure. Of course, in the near future, as artificial intelligence (AI) systems become more powerful, we will also see more automated and increasingly complex social engineering attacks. Various types of cyber attacks with AI are bound to lead to the explosion of network penetration and the theft of personal data, as well as the intelligent spread of computer viruses.
The irony is that we are still hoping to use AI to defend against all kinds of attacks with AI. As the saying goes: The road is one foot high and the height is one foot. This development is likely to lead to the AI-style "arms race", and the consequences will only become more and more complicated.