The Internet of Things without security is not an Internet of Things!
The Internet of Things without security is not an Internet of Things! This has become the basic consensus of everyone in the Internet of Things era.
According to statistics, by 2020, there will be 50 billion devices connected to the Internet of Things in the world. Considering the diversity of interconnected communication links and cloud deployments, it is conceivable to maintain the complexity of the security of such a large network system. Some analysts pointed out that 83% of the attacks targeting the Internet of Things are targeted at edge devices, and the largest group of tens of billions is the most unpredictable security in the Internet of Things. "Short board".
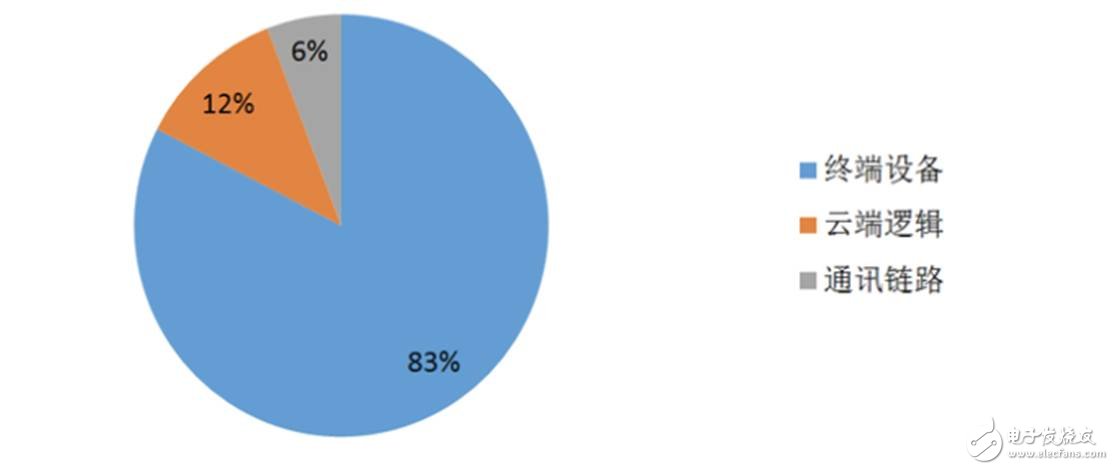
[ Figure 1: In the security attack against the Internet of Things, a large number of terminal devices have become the main target]
More deadly, in the eyes of hackers, edge devices are not their ultimate target. They will use the edge device as an attack interface and become a convenient "gate" for invading the Internet of Things. In this regard, Shijian company senior product manager Terence Li said:
 Once an intruder enters (or spoofs) an IoT node into the IoT network, the security of the entire network becomes more vulnerable. They can steal important databases, undermine normal workflows, access them through cloud services, and control the operation of the nodes themselves, which is hard to estimate. Therefore, the security protection of Internet of Things edge devices is gradually becoming the highlight of IoT development. In short, we need to add a “security door†to the edge devices of the Internet of Things to keep possible security threats out of the door. Once an intruder enters (or spoofs) an IoT node into the IoT network, the security of the entire network becomes more vulnerable. They can steal important databases, undermine normal workflows, access them through cloud services, and control the operation of the nodes themselves, which is hard to estimate. Therefore, the security protection of Internet of Things edge devices is gradually becoming the highlight of IoT development. In short, we need to add a “security door†to the edge devices of the Internet of Things to keep possible security threats out of the door.
Once an intruder enters (or spoofs) an IoT node into the IoT network, the security of the entire network becomes more vulnerable. They can steal important databases, undermine normal workflows, access them through cloud services, and control the operation of the nodes themselves, which is hard to estimate. Therefore, the security protection of Internet of Things edge devices is gradually becoming the highlight of IoT development. In short, we need to add a “security door†to the edge devices of the Internet of Things to keep possible security threats out of the door. Once an intruder enters (or spoofs) an IoT node into the IoT network, the security of the entire network becomes more vulnerable. They can steal important databases, undermine normal workflows, access them through cloud services, and control the operation of the nodes themselves, which is hard to estimate. Therefore, the security protection of Internet of Things edge devices is gradually becoming the highlight of IoT development. In short, we need to add a “security door†to the edge devices of the Internet of Things to keep possible security threats out of the door. 
So what kind of edge device is a safe IoT node? Some people have summarized the basic elements of their security as "CIA."
Confidentiality: Data stored or being sent should be visible only to the licensor;
Integrity: Messages sent should not be modified before reaching the destination;
Authenticity: It can be assured that "the sender of the message is the claimed person."
In order to achieve the goal of "CIA", it is common practice to use a key or a private key as a unique part of the verification identification tag, and to manage the storage and communication of these keys to ensure the security of the system. Although there are many security technologies that can meet the above requirements, developers will still find it difficult to implement them.
There are two reasons for this. First, edge devices are often very "simple" and it is difficult to equip "security" with redundant resources. Any security strategy needs to balance computing power, memory, power, cost and more. Second, developers lack targeted, easy-to-use "tools" to solve this problem efficiently.
Terence Li, senior product manager at Shijian, said:
 The good news is that such 'tools' are now available! This is the cryptographic component - it is integrated into the edge device, not only can be used as a hardware crypto accelerator instead of the main processor to complete the complex encryption and decryption algorithm, but also ensure that the key involved in the encryption operation must be stored in a hidden protection. In the hardware, ensure that the key is 'transparent' invisible in software or unprotected hardware. ATECC508A, the latest addition to Microchip's family of cryptographic components, is the most iconic of its kind.
The good news is that such 'tools' are now available! This is the cryptographic component - it is integrated into the edge device, not only can be used as a hardware crypto accelerator instead of the main processor to complete the complex encryption and decryption algorithm, but also ensure that the key involved in the encryption operation must be stored in a hidden protection. In the hardware, ensure that the key is 'transparent' invisible in software or unprotected hardware. ATECC508A, the latest addition to Microchip's family of cryptographic components, is the most iconic of its kind. 
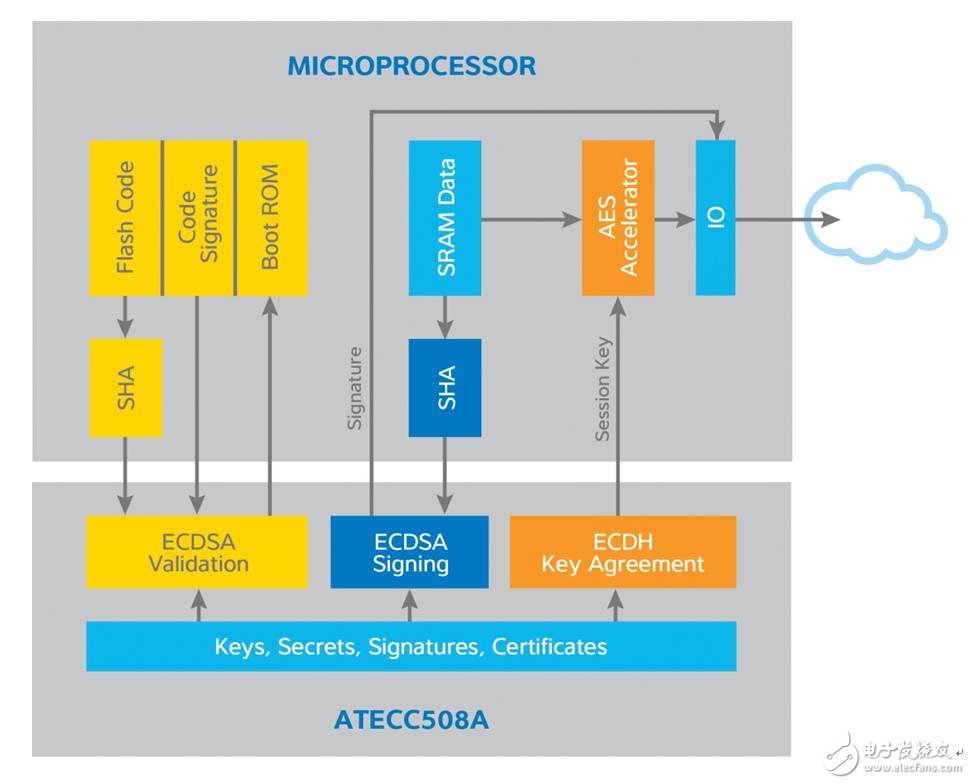
[ Figure 2: ATECC508A works with the microprocessor to achieve the safety requirements of the edge device "CIA"]
ATECC508A supports both Elliptic Curve Digital Signature Algorithm (ECDSA) and Elliptic Curve Key Exchange (ECDH). Simply add an ATECC508A to the IoT edge node to easily and efficiently implement confidentiality, integrity and authentication mechanisms.
The ATECC508A uses a single bus or I2C bus communication with a small number of pins, a minimum package size of only 2mm × 3mm, and a standby sleep current of less than 150 nanoamps. So with a small cost and resource budget, you can add it to your edge devices.
ATECC508A receives the input provided by the processor, performs calculations internally and returns calculation results such as signature, authentication, session key, etc., and does not leak the calculation method during the whole process. A high quality True Random Number Generator (TRNG) helps to successfully prevent transactions from being played back. Internal serial numbers help ensure the uniqueness of the key, while large-capacity counters can be used to track the authentication process.
In addition, to guard against adjacent attacks and physical attacks, the ATECC508A has been specially designed—the entire chip is covered with a serpentine metal pattern that prevents internal signal release from being detected externally and provides visual impairments that prevent the attacker from opening the package to the chip. Internal observation and detection operations. At the same time, the device protection case is connected to the rest of the circuit. If the protection case is broken, the chip will no longer operate, in case the attacker obtains the key by detecting the circuit node.
Terence Li, senior product manager of Shijian Company, concluded that:
 The ATECC508A supports configuration during production, and the configuration can be easily accomplished using a simple module to ensure that keys and signature certificates are securely inserted into the cryptographic component. This configuration process can be performed by Microchip or by an authorized dealer such as Excelpoint to provide technical support and convenience to the user.
The ATECC508A supports configuration during production, and the configuration can be easily accomplished using a simple module to ensure that keys and signature certificates are securely inserted into the cryptographic component. This configuration process can be performed by Microchip or by an authorized dealer such as Excelpoint to provide technical support and convenience to the user. 
With the tools of ATECC508A, developers can immediately build a "security door" for the edge of the Internet of Things .

[ Figure 3: ATECC508A can be easily configured in production ]
Comcn Electronics Limited , https://www.comencnspeaker.com