Analysis of the working principle of dma technology
DMA technology is an abbreviation of Direct Memory Access. It means "memory direct access." It refers to a high-speed data transfer operation that allows direct reading and writing of data between external devices and memory, neither by the CPU nor by CPU intervention.
DMA refers to an interface technology in which an external device exchanges data directly with system memory without passing through a CPU. To read the data of the peripheral into the memory or transfer the data of the memory to the peripheral, it is usually done by CPU control, such as CPU program query or interrupt mode. Using interrupts for data transfer can greatly increase CPU utilization. However, the use of interrupt transfer has its shortcomings. For a high-speed I/O device and bulk exchange of data, only DMA can be used to solve the efficiency and speed problems. The DMA exchanges data directly between the peripheral and the memory without going through the CPU, so the speed of data transfer depends on the speed at which the memory and peripherals work.
The entire data transfer operation is performed under the control of a so-called "DMA controller". In addition to a little processing at the beginning and end of the data transfer, the CPU can perform other tasks during the transfer. Thus, most of the time, the CPU and input and output are in parallel operation. Therefore, the efficiency of the entire computer system is greatly improved.
DMA principleDMA principle: DMA (Direct Memory Access) is an important feature of all modern computers. It allows hardware devices of different speeds to communicate without relying on a large amount of interrupt load on the CPU. Otherwise, the CPU needs to copy the data for each fragment from the source to the scratchpad and then write them back to the new location. During this time, the CPU is not available for other jobs. A DMA transfer copies data from one address space to another. When the CPU initiates this transfer action, the transfer action itself is executed and completed by the DMA controller. A typical example is moving a block of external memory to a faster memory area inside the chip. Such an operation does not delay the processor's work, but can be rescheduled to handle other work. DMA transfers are important for high performance embedded system algorithms and networks.
When implementing DMA transfer, the DMA controller directly controls the bus. Therefore, there is a problem of bus control transfer. That is, before the DMA transfer, the CPU must give the bus control to the DMA controller, and after the DMA transfer is finished, the DMA controller should immediately return the bus control to the CPU. A complete DMA transfer process must go through the following four steps.
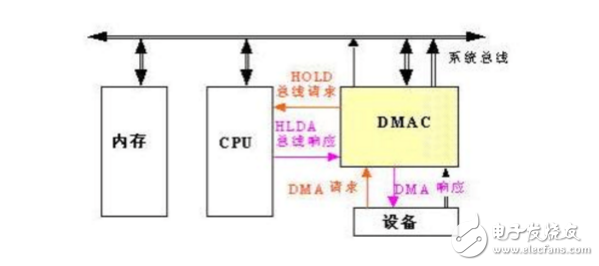
1.DMA request
The CPU initializes the DMA controller and issues an operation command to the I/O interface, and the I/O interface issues a DMA request.
2. DMA response
The DMA controller discriminates the priority and masking of the DMA request and issues a bus request to the bus arbitration logic. The bus control is released when the CPU executes the current bus cycle. At this point, the bus ruling logic outputs a bus acknowledgment indicating that the DMA has responded, informing the I/O interface to initiate a DMA transfer via the DMA controller.
3. DMA transmission
After the DMA controller gains control of the bus, the CPU immediately suspends or performs only internal operations. The DMA controller outputs read and write commands to directly control the RAM and the I/O interface for DMA transfer. Under the control of the DMA controller, data transfer is directly performed between the memory and the external device, and the participation of the central processing unit is not required during the transfer. Start with the starting position and data length of the data to be transferred.
4. DMA ends
When the specified batch data transfer is completed, the DMA controller releases the bus control and sends an end signal to the I/O interface. When the I/O interface receives the end signal, it stops the operation of the I/O device on the one hand, and requests an interrupt request to the CPU on the other hand, so that the CPU is free from the state of not intervening, and performs a check to check the correctness of the DMA transfer operation. Code. Finally, continue with the original program with the results and status of this operation.
It can be seen that the DMA transmission mode does not require the CPU to directly control the transmission, and does not have the process of reserving the scene and restoring the scene as in the interrupt processing mode. The hardware opens a direct data transmission path for the RAM and the I/O device, so that the efficiency of the CPU is greatly improved. improve.
Second, the emergence of DMA transfer mode DMA technology ,
This allows the peripheral device to directly access the memory through the DMA controller, while the CPU can continue to execute the program. So how do DMA controllers and CPUs use memory when they are split? The following three methods are usually used:
(1) Stop the CPU access;
(2) periodic appropriation;
(3) DMA and CPU alternate access to memory.
1. Stop CPU access to memory
When the peripheral device requests to transfer a batch of data, the DMA controller sends a stop signal to the CPU, asking the CPU to abandon the use of the address bus, the data bus, and the associated control bus. After the DMA controller gains control of the bus, data transfer begins. After a batch of data transfer is completed, the DMA controller notifies the CPU that it can use the memory and returns the bus control to the CPU. Figure 8.16(a) is a time diagram of this type of transmission. Obviously, during this DMA transfer, the CPU is basically in an inactive state or a hold state.
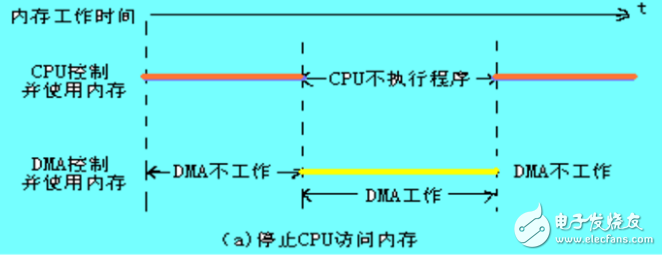
Advantages: Simple control, it is suitable for group transfer of devices with high data transfer rate.
Disadvantages: In the DMA controller access phase, the memory performance is not fully utilized, and a considerable part of the memory work cycle is idle. This is because the interval between the transfer of two data by the peripheral is generally always greater than the memory storage cycle, even for high-speed I/O devices. For example, a floppy disk requires approximately 32 us to read an 8-bit binary number, while a semiconductor memory has a storage period of less than 0.5 us, so many free memory cycles cannot be utilized by the CPU.
2. Periodic stealing : When the I/O device does not have a DMA request, the CPU accesses the memory according to the program requirements; once the I/O device has a DMA request, the I/O device steals one or several memory cycles.
The timing of this transfer method is as follows:
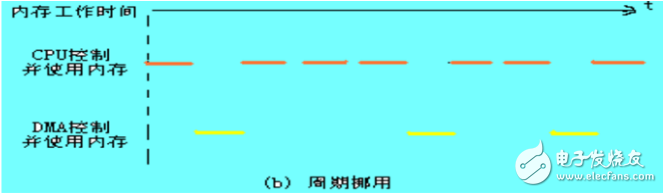
I/O devices may encounter two situations when DMA transfers:
(1) At this time, the CPU does not need to be accessed, for example, the CPU is executing the multiplication instruction. Since the multiplication instruction execution time is long, there is no conflict between the I/O access and the CPU access, that is, the I/O device stealing one or two memory cycles has no effect on the CPU execution program.
(2) When the I/O device requests access to the CPU, the CPU also requests an interview. This creates an internal conflict. In this case, the I/O device access priority, because there is time requirement in the I/O access, the previous one. I/O data must be accessed before the next request is made. Obviously, in this case, the I/O device steals one or two memory cycles, which means that the CPU delays the execution of the instruction, or more specifically, inserts the DMA request during the execution of the internal instruction by the CPU, and steals one. Two memory cycles. Compared with the DMA method of stopping CPU access, the method of cyclic stealing not only realizes I/O transmission, but also exerts the efficiency of memory and CPU well, and is a widely used method. However, every period of I/O device stealing has the process of applying bus control, establishing line control and returning bus control. Therefore, it takes one cycle to transfer one word to memory, but it is generally necessary for DMA controller. 2-5 memory cycles (depending on the delay of the logic). Therefore, the method of periodic stealing is applicable to the case where the I/O device read/write period is greater than the memory storage period.
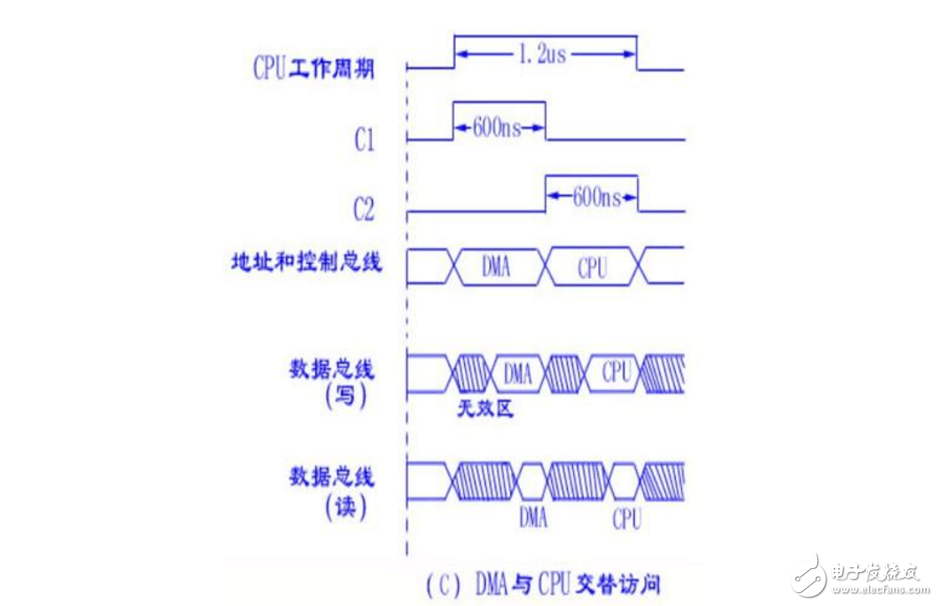
3.DMA alternately access the CPU and if the duty cycle is much longer than the CPU memory access cycle, the method used at this time in the alternate access and CPU allows the DMA transfer simultaneously achieve maximum efficiency. Assuming that the CPU duty cycle is 1.2μs and the memory access cycle is less than 0.6μs, then one CPU cycle can be divided into two sub-cycles, C1 and C2, where C1 is used for DMA controller access and C2 is reserved for CPU access.
The timing of this transfer method is as follows:
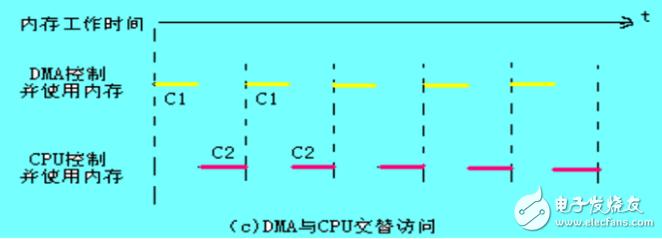
The next page is a detailed time chart of the DMA and CPU alternate access. Assuming that the CPU duty cycle is 1.2us and the memory access cycle is less than 0.6us, then one CPU cycle can be divided into two sub-cycles, C1 and C2. C1 is reserved for DMA controller access, and C2 is reserved for CPU access.
This method does not require the application, establishment and return process of the bus usage rights, and the bus usage rights are time-sharing through C1 and C2. The CPU and DMA controller each have their own control register such as an internal address register, a data register, and a read/write signal. In the C1 cycle, if the DMA controller has an intra-access request, a signal such as an address or data can be sent to the bus. In the C2 cycle, if the CPU has an intra-access request, the address, data, and the like are also transmitted. In fact, for the bus, this is a multiplexer controlled by C1, C2. This transfer of bus control power takes almost no time, so the efficiency is very high for DMA transfer.
This type of transfer is also known as the "transparent DMA" method. The reason for this DMA transfer is that the CPU, like transparent glass, has no feeling or influence. Working in a transparent DMA mode, the CPU does not stop the main program or enter the wait state, which is an efficient way of working. Of course, the corresponding hardware logic is more complicated.
China manufacture for Popular Custom Vape Pen, high quality battery, quality e-liquid and food safty material.
Prefilled Vape
Newmax Electronics Co.,Limited , https://www.advvape.com