Use dynamic software analysis to support medical device approval
Medical equipment that includes software systems is like building complex systems. Manufacturers face the same challenges: time, quality, scale (number and complexity of functions), and cost. In addition, the product also needs to pass the approval of local regulatory authorities, such as the US Food and Drug Administration (FDA), the European Union Medical Device Directive (MDD), the British Drug Administration (MHRA) and other similar regulatory agencies.
In this article, we will discuss how dynamic code analysis can help medical devices demonstrate security compliance and the key functions that dynamic analysis tools should have. To help designers choose an operating system (OS), the article also briefly describes which features of the OS can promote the design, development, and approval process of security-related software.
Expertise and process
Professional knowledge and a good development process do not ensure that the system meets the required reliability, or even that it is a good system. But these two really can greatly increase this possibility.
The simple design required to create safety-critical systems requires exceptional expertise. To prove that the tested software system meets the safety requirements, a thorough and thorough understanding of the software verification method, the evaluated software, and the evaluation environment (including verification of similar systems) is required.
There is no doubt that the IEC62304 standard focuses on the development process. Understanding this, our work will be better, not only for software development in an environment that meets the most stringent quality management standards, but also to use tools to help ensure that our systems meet these standards and report to the auditors And the supervisory authority to provide evidence to prove.
Demonstrate reliability
To ensure approval by regulatory agencies, manufacturers must prove that these devices meet safety specifications. For device software, it is necessary to prove that they meet the requirements of trust (reliability and availability) standards. Whether it meets the reliability or availability requirements depends on the use of the system. The detailed requirements and precise credibility requirements provide established premises and precise methods to help us verify the credibility of software systems.
Define acceptable risk
No software system is absolutely reliable. Even if the system is absolutely reliable, we cannot prove it. The available methods cannot prove that the system will never fail. They can only help us find and avoid errors and estimate the probability of failure. Therefore, when the failure rate of the software system is low enough and there is no unacceptable risk, it is "safe". The precise meaning of "unacceptable risk" or "acceptable risk" varies by industry and administrative jurisdiction. Measurement methods include:
Ø ALARP (As Low as Reasonably PracTIcal): define and classify potential hazards and related risks as: a) clearly unacceptable, b) tolerable if the removal cost is too high, and c) acceptable accept. All unacceptable risks must be removed, but the tolerable risks will only be removed when the cost and time of removal are reasonable.
Ø GAMAB (globalement au moins aussi bon) or GAME ((globalement au moins équivalent): The risk level of the new system should be at least roughly equal to the risk level of the existing system.
Ø MEM (Minimum Endogenous Mortality): In the field of new system deployment, the mortality rate it brings cannot exceed one tenth of the conventional mortality rate in the region. For example, for people in their 20s in Western countries, this value is about 0.0002.
All these methods need to be adjusted according to the actual situation, mainly depending on the number of people that may be affected by the serious failure of the equipment. When using the ALARP method, in order to determine which risks are unacceptable, which are tolerable, and acceptable, we need to determine the maximum probability of failure allowed for serious failures of each risk. If the GAMAB and MEM guidelines are used, we need to determine this value globally.
Proof of software reliability
At present, no single method is sufficient to prove that software systems meet reliability requirements. Therefore, our reliability demonstration must use a combination of various methods and techniques, including but not limited to:
Ø Development environment that meets the requirements of IEC 62304 and other similar standards
Ø Requirements tracking matrix to ensure that all safety related requirements have been met
Ø Formal design methods and tools can provide mathematical basis for the correctness of the design
Ø Fault tree analysis using Bayesian belief network method
Ø Retrospective design verification, evaluate system design based on completed work
Ø Static analysis, using methods such as model checking or data flow analysis
Ø Use direct fault detection technology for testing, such as dynamic analysis, to identify faults through generated errors and failures
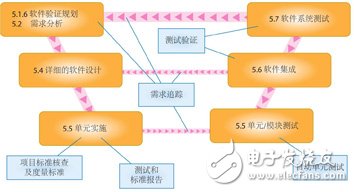
Figure 1 The different analysis methods and relevant chapters involved in the IEC 62304 standard are represented by a typical "V" shaped development model. Each method shown in the figure does not depend on the process. Any other development process model can be similarly expressed: waterfall, iterative, sensitive, etc.
Benefits of Privacy Screen Protectors
As a personal item, a mobile phone will always contain all kinds of private information and secrets. Therefore, when many people use their mobile phones in public places, they are worried that their screen content will be seen by the people next to them. Especially when you use your mobile phone to enter various passwords, it is very dangerous if you are targeted by malicious people.
In order to prevent private information and confidential documents from being peeped, Privacy Screen Protector came into being. As the name suggests, it is a Mobile Phone Screen Protector, which can prevent others from prying on the screen and protect personal privacy. When you install a Privacy Screen Protector on your phone, people around you won't be able to see what's on your screen.
The Anti-Spy Screen Protector uses patented ultra-fine louver optical technology, so that the information on the screen is displayed on the front for the user to read. The viewable area is 60 degrees. Anyone can only see the dark picture on both sides. And the anti-blue light effect of the Privacy Screen Protective Film, the blue light blocking rate is about 10%-30%, and the mobile phone with the Privacy Film will automatically darken to reduce some glare. Therefore, normal use will not hurt the eyes, but will play a protective role. Anti-peeping Screen Protector effectively protect business secrets and personal privacy. Whether it is work, study, communication or entertainment, it makes the use of computers and mobile phones more free. Help the company's senior business personnel, lawyers, consultants, financial personnel, etc. to avoid screen information leakage when using mobile phones.
Anti-Peep Hydrogel Screen Protector,Anti-Spy Tpu Hydrogel Film,Privacy Hydrogel Protector,Privacy Screen Protector Sheet
Shenzhen TUOLI Electronic Technology Co., Ltd. , https://www.hydrogelprotectors.com